Media release
From:
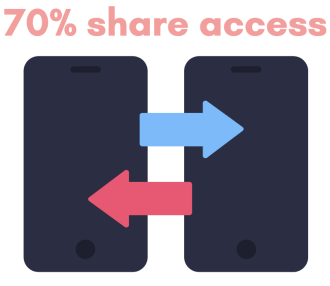
Does your partner know the password to your phone? Probably.
A study by Griffith University researchers reveals that 70 per cent of Australians share access to their phone with their partner, despite dominant cybersecurity guidelines advising the opposite.
Professor of Criminology and Criminal Justice, Molly Dragiewicz, who led the study with Dr Jeffrey Ackerman and research assistant Marianne Haaland, said the most common reasons for smartphone sharing were positive, but that does not guard against negative impacts.
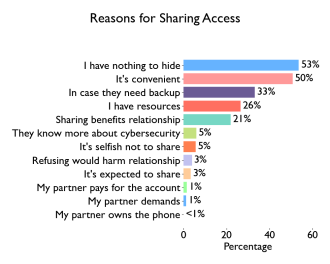
“People usually share for convenience, out of trust, and to help each other,” Professor Dragiewicz said.
“However, if one partner turns out to be abusive later on, shared access can be dangerous.”
In fact, 20 per cent of identity theft perpetrators identified by Australian police are current or former intimate partners or individuals related to an ex-partner.
In addition, technology-facilitated abuse is a common component of coercive control.
The report’s findings show that younger people are more likely to share, suggesting this is a growing issue.
Professor Dragiewicz argues that the one-user/one-device threat model created for commercial and government contexts is inadequate for addressing interpersonal cybersecurity risks.
Phone and app design can help to reduce the risks by using Safety by Design, as recommended by the Australia’s eSafety Commissioner.
“Cybersecurity advice and design based on not sharing your device or credentials are a really bad fit with how people actually use their phone.
The first step in Safety by Design is understanding how technology is used in real life,” Professor Dragiewicz said.
The study was made possible by a grant from the Australian Communications Consumer Action Network (ACCAN).
Multimedia








 Australia; QLD
Australia; QLD



